Cryptology - I: Exam 1 - Classical Cryptology + DES
Exam 1 covered from the beginning of the class up to and including
the discussion of the DES encryption algorithm. Cryptanalysis of DES
was not included.
Rules. The following constraints hold for Exam 1:
- Open-book but not open notes.
- GRAD and UNDERGRAD students: Answer BOTH #3 and #5
- GRAD students......................................:
Answer ONLY TWO of #2, #4, #6, or #7
- UNDERGRAD students ....................:
Answer ONLY TWO of #1, #2, #4, #6, or #7
- The University's Academic Honesty Policy holds.
Problem 1. Shift Cipher.
Given: Polish cryptography has reportedly declined in sophistication
since their "glory days" with the Enigma Machine. They are now reduced
to industrial espionage. A man named von Barjinsky has been accused
of passing industrial secrets from a major nation to terrorists in
the Middle East. You are the agent in charge of the crypto room
when the following message comes in, complete with inter-word spaces.
The message is ciphertext generated from English plaintext by mono-
alphabetic shift cipher. The numbers (e.g., 600) are unencrypted.
You are told that this is a secret message about a crystal lens that
is being used to focus dangerous radiation. Your assignment is to
decrypt the message using statistics of single-symbols and digrams.
Given the clues, this is an easy task if you think about the known
structure of the English language, as well as properties of the
shift cipher. A few facts from high-school physics might also be
helpful.
Ctxt:
KMBICDKVNSPPBKMDSYXVOXCGKCMYXCDBEMDKDKBQYXXOXKDSYXKV
VKLYBKDYBIPYBECOKCKDOVOCMYZODYPYMECXEMVOKBQKWWK
BKICSDMYXCSCDONYP600CSXQVOMBICDKVCYPQOBWKXSEW
KBBKXQONSX8MYXMOXDBSMBSXQCDROWYEXDONKXQVOYPOKMR
MBICDKVGKCKNTECDONDYSXDOBMOZDKXNNSPPBKMDDROSXMYWSXQ
QKWWKBKICGSDRKXKMMEBKMIYPKPOGKBMCOMDROZOBPYBWKXMO
YPDROVOXCGKCDOCDONSXDGYGKICSXYXOMKCODROQKWWK
BKICGOBOPYMECONYXCSXQVOWONSEWCSJOQOBWKXSEWNODOMDYB
SXDROCOMYXNMKCODROQKWWKBKICGOBOPYMECONYXDRO
MOXDBKVQOBWKXSEWNODOMDYBYPK3H3WKDBSHYPCWKVVQOBWKXSEW
NODOMDYBCDROOPPSMSOXMISWKQOMYXMOXDBKDSYXKXNSWKQO
AEKVSDIKXNCRKZOGOBOWOKCEBONDRODOCDCZOBPYBWONGSDR
DRO3H3WKDBSHNODOMDYBCICDOWGOBOZKBDSMEVKBVISXDOBOCDSXQ
The following questions contain keywords to search for:
[1pt]What kind of Rays were focused? Ans: Gamma Rays
Method: Construct the following table and look for
the encryption of ray (a trigram is usually sufficient):
Char Maps-to...
----+----------------------------------------
r | s t u v w x y z a b c d e f g h i j k...
a | b c d e f g h i j k l m n o p q r s t...
y | z a b c d e f g h i j k l m n o p q r...
The shift a |-> k is found at the beginning of the third row
(i.e., ray |-> BKI). In English,
modifiers appear before nouns, so look at the last ten characters
of the second line of ciphertext. The last five letters,
which are QKWWK, decrypt to gamma.
[1pt] How many small Detectors were used? Ans: 3x3 array = 9
detectors
Method: Find the numbers (e.g., 600, 8, 3H3). Look
at the text around them, and decrypt the surrounding ciphertext
using the shift deduced above. You find that a 3x3 array of small
detectors was used. Since 3x3 = 9, there were nine detectors
employed.
[3pt] Now that you have all the important clues, write the first
four plaintext sentences.
Ans: A crystal diffraction lens was construct at Argonne
National Laboratory for use as a telescope to focus nuclear
gamma rays. It consisted of 600 single crystals of germanium
arranged in 8 concentric rings. The mounted angle of each crystal
was adjusted to intercept and diffract the incoming gamma rays
with an accuracy of a few arc sec. The performance of the lens
was tested in two ways.
Method: If you don't already know the shift, you can
use the brute-force method of trying the 26 possible decryptions
of, say, the first ten characters in the message. Recognizable
words will appear when the correct shift position is discovered.
Problem 2. Traffic Analysis with Substitution Cipher.
Given: You are a WWII spy assigned to watch the Five Islands area,
which consists of Islands A, B, C, D, and E (actual names).
You are on Island A and can see Islands B, C, and E. The
latter is uninhabited, with a small harbor but no water. You
suspect that there is an island (D) over the horizon, since
you can see puffs of smoke that spell out Roman letters
in Morse Code. There are frequent exchanges of messages
between Islands B and C, who occasionally send armed vessels
cruising around the waters, but appear not to be conducting
warfare. Later that day, you see the following message
that appears to be Javanese [a real language] coming from
island D, then what looks like a garbled alphabet coming
from island B, the one closest to you.
Ctxt-D: luiyyihaiiyoile Ctxt-chars (order of use): luiyhaole
Ctxt-B: aeiouoklmnptyoa Ctxt-chars (order of use): aeiouklmnpty
Ptxt-B: WEGOTOISLND_NOW Ptxt-chars (order of use): WEGOTISLND_N
Wanting to make a good impression your first week on the job,
you consult your handy Javanese dictionary and fail to
find words that make sense. You guess that the first message
must be decrypted, but can't immediately find the key.
Instead, you recall your Crypto-I class discussion of traffic
analysis and find that Ctxt-B is easily decrypted using a
substitution, as shown above, except for one character,
which you think may be a vowel. You guess that Ctxt-D has a
similar encryption scheme but a simpler ciphertext (ctxt)
alphabet, and a different key. You also know that the plain-
text used by Island D's chief uses a vowel (an island name)
as its most frequent letter. The island in question is the
one on which he had a love affair for several years.
Complete Ptxt-B correctly, decrypt Ctxt-D, and choose the
safest appropriate action, based on givens, alternatives
A-N, as well as common sense :)
Scoring: 1 point for Ptxt-B and 3 points for Ptxt-D, 1 point for
the correct answer chosen from the list below (there is
only one correct answer).
Actions: (Choose only one)
A) the Chief of Island D is asking the Chief of Island B to go
fishing, so you can relax and enjoy island life;
B) the Chief of Island D is asking B if there are any islands
nearby, and B says that yours is the only one. Prepare
for trouble in the weeks ahead;
C) you should paddle quickly to Island B;
D) you should paddle by obvious route to Island C;
E) you should paddle by obvious route to Island D;
F) you should paddle by hidden route to Island E;
G) you should paddle by hidden route to Island C;
H) you should paddle by hidden route to Island D;
I) you should paddle by obvious route to Island E; or
J) you should stay on Island A, as the message does not concern you
K) A and G L) B,G, and D M) C or B N) none of the above
Method: The following steps suffice to produce a solution via
traffic analysis and a small amount of cryptanalysis:
- There are five islands, A-E, of which B and C communicate
regularly and send ships back and forth, but not for
warfare. Thus, we can hypothesize that B and C are either
friendly or neutral toward each other.
- Signals come from Island D, which are acknowledged (or
replied to by Island B as: "We go to Island __ now".
One can hypothesize that D and B know each other, and are
headed for another island, i.e., A, C, or E. However,
island E has a small harbor but no water and is uninhabited,
so more reasonable choices for destinations are A and C.
- The givens say that the island name in Ptxt-B is likely a
vowel. This narrows the choice to A, which is your island.
Also, if we note (from the givens) that A is the most
frequent character in the alphabet of Ctxt-D, then we have
the following trial decryption of Ctxt-D:
Ctxt-D: luiyyihaiiyoile
Ptxt-D? --a--a--aa--a--
Noting the oddity of the double letters between the first
two a's, we observe that y in Ctxt-D
could only be a consonant in English. A dictionary search
yields y = T to be common choice. This gives:
Ctxt-D: luiyyihaiiyoile
Ptxt-D? --atta--aat-a--
which can be hypothesized to mean:
Ctxt-D: luiyyihaiiyoile
Ptxt-D? --attackaat-a--
i.e., ...attack A at...
- Now, it appears that B and D are headed toward island A,
with hostile intent. What does one do? One cannot escape
safely to island C, since C and B appear to have a non-hostile
relationship. Since A and E are the sole remaining choices,
and you want to leave A, E is the only choice. Since we do
not know if B or D can see E, it is best to move to E by
hidden route (answer F).
Problem 3. Histogram Manipulations (moments)
The following message in Hawaiian: "okoualohanoaikaikalani"
"lhnln"
is a line from a famous song. Compute its:
[1pt] a) histogram:
Ans: Letting the alphabet F = {a,e,i,o,u,h,k,l,m,n,p,w},
the histogram is given by (6,0,3,4,1,1,3,2,0,2,0,0) which looks like:

[1pt] b) modal character
Ans: A occurs most frequently
[1pt] c) median character
Ans: N = 22 = 6+3+4+1+1+3+2+2, and the
median threshold is N/2 = 11. Given the cumulative
histogram c = (6,6,9,13,14,15,18,20,20,22,22,22),
we see that the median is reached at the fourth character
given the ordering inherent on F Thus, the
median is found at "O". Note that
the answer will vary depending upon how F is ordered.
For example, if lexicographical order is used ([aehiklmnopuw]),
then the histogram and cumulative histogram would
have a differently ordered domain, and the median would be
different. (Compute these values as an exercise.)
[1pt] d) mean character
Ans: Mean = N/|F| = 22/12 = 1.833,
using the alphabet specified in (a). If a different
alphabet is used, the mean will be different.
[1pt] e) standard deviation about the mean, assuming F
is indexed by {1,2,...,N}.
Ans: Using the standard formula for the
standard deviation  we have
we have
(for the histogram shown in a), above),
 (h) =
(N-1 ·
[(6-1.833)2 + (4-1.833)2 +
2 · (3-1.833)2 +
2 · (2-1.833)2
(h) =
(N-1 ·
[(6-1.833)2 + (4-1.833)2 +
2 · (3-1.833)2 +
2 · (2-1.833)2
+
2 · (1-1.833)2
4 · (0-1.833)2])1/2,
which yields  = 1.34 .
= 1.34 .
Problem 4. PROBLEM 4. Transposition Cipher
[5pt] Use your knowledge of digram and trigram statistics to decrypt
the following transposed ciphertext. Show your work to obtain
credit.
Ctxt: htiwelhresunegoaarthenteastuerpirrowlvduaherbuigothnts
nctauscseteoshttgiresenocnairgtonehwtahahesodecsnniezz
Method: One approach is to perform the following steps:
- Observe that there are two z's at the end of the
ciphertext (a giveaway). Assuming the last two characters
are "padding", we see that N = 108.
- Factoring N, we obtain 2x94, 3x36, 4x47, 6x18, and 9x12.
- Trying 2 and 4 as blocklengths, we see that no intelligible
text results from any permutation. The same is true of a
blocklength of 6.
- However, looking at the introductory text, we see that
the phrase while there might be present in the first
ten letters. Let's try to fit that hypothesis to a block
length of 9:
Index: 123456789 123456789 123456789 123456789 ...
Ctxt.: htiwelhre sunegoaar thenteast uerpirrow ...
Xpos1: 4736-21-8 473652198 473652198
Ptxt1: whilether eanogusra naeethtts (Wrong!)
Xpos2: 4136-27-8 413652798 413652798 413652798 ...
Ptxt2: whilether esnoguara nteethats purrierwo ...
On the first attempt, (Xpos1,Ptxt1), we
recognize that there are two h's and two e's,
and put dashes in the e positions. By permuting the
h positions, we can obtain recognizable plaintext
on the second attempt (Xpos2,Ptxt2).
- Dividing the ciphertext into blocks of nine characters
and applying the transposition
Xpos2, we
obtain the plaintext:
"While there's no guarantee that Spurrier would
have brought instant success to the Tigers, one
can't ignore what he has done since."
-- From the Alligator 10/96
A similar result could have been obtained by marking the h's
with dashes first, then permuting the positions corresponding to
e's.
Problem 5. Rotor Machine
[1pt] a) What is the role of the Steckerboard in the Enigma Machine?
Ans: The Steckerboard is a programmable substitution that was
designed to increase the security of the Enigma machine by
providing initial "confusion" (in the sense of Shannon). The
Steckerboard substitution is composed with the polyalphabetic
cipher implemented by the rotors.
[2pt] b) How effective is the Steckerboard? Justify your answer
mathematically.
Ans: The Steckerboard is not as effective as its designers
thought, because it does not change with the input, as the rotors
do. Thus, given known plaintext and ciphertext, the Steckerboard
setting can be easily determined by differential cryptanalysis.
Additionally, the Steckerboard is inverted as the last step of
the Enigma encryption. Denoting the
plaintext as a, the rotor cipher as f,
and the Steckerboard substitution as S, we express the
Enigma encryption as:
e(a) = S-1(f[S(a)]),
which implies that the inverse Steckerboard substitution is included
in the ciphertext. This clearly provides information on S
to an adversary, which decreases the security of the Enigma machine.
[2pt] c) What function did the reflector perform in the Enigma machine?
Give an example.
Ans: The reflector effectively doubled the number of rotors
by sending the text encrypted in the forward pass through the
rotors back through the rotor stack, but by a different path.
Given N rotors, the effective number of rotors (N') became
2N < N' < 2N+1. A drawing of a two-rotor machine with reflector
would suffice here.
Problem 6. Vigenere Cipher (histogram attack)
[2pt] a) Given the following probability distribution of a plaintext corpus
that has an alphabet of four letters:
Pr(f) = (0.08,0.24,0.36,0.32), f in {A,B,C,D},
construct the likely ciphertext probability distribution if the key
has the following shifts: k = (-1,-2,0,0).
Ans: This is a simple calculation, as follows:
0 shift: (0.16,0.48,0.72,0.64) -- taken twice
-1 shift: (0.24,0.36,0.32,0.08)
-2 shift: (0.36,0.32,0.08,0.24)
------------------------------- -- Add Pointwise
b = (0.76,1.16,1.12,0.96) -- Non-normalized result
Normalizing the sum of b to 1.0, we obtain
Pr(c) = (0.19,0.29,0.28,0.24) .
[1pt] b) If the ciphertext frequency distribution is nearly even,
then what characteristics do you expect the key to have?
Illustrate your answer with a numerical example.
Ans: This is another simple problem. If Pr(c) is uniform,
then all possible key shifts are represented once, and the key is
comprised of those shifts. This makes determination of the key
length easy, since it will be a multiple of the alphabet size.
The preceding assertion can be easily verified by noting that the
number of possible shifts over an alphabet F is equal to
|F|. An example similar to the one above, where |F|
< 4 would suffice (i.e., a 2- or 3-character alphabet).
[2pt] c) Under what conditions is the Kasiski attack infeasible?
Justify your answer with supporting arguments.
Ans: The Kasiski attack is infeasible when the period of the
Vigenere cipher is large in relationship to the alphabet size.
The Kasiski constraint says that two identical segments of
plaintext will be encrypted to the same ciphertext when they
occur in the plaintext at x positions apart, where
x 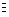 0 mod m,
where m denotes the keyword length.
0 mod m,
where m denotes the keyword length.
In practice, we search the ciphertext for pairs of identical segments
and tabulate the distance between the starting points of each
element in a given pair. Thus, we have two primary implementational
problems if the cipher period N is too long, namely,
- N may exceed the length of the ciphertext,
which is certainly possible in the rotor machine. In
this case, there is no ciphertext repetition.
- N may be sufficiently long that the
ciphertext repeats only once or twice, and the actual
distances cannot be distinguished from false repetitions,
which may occur the same number of times.
A useful example of an encryption that cannot usually be attacked with
the Kasiski cipher is a three-rotor Enigma machine with reflector,
implemented over the alphabet A-Z.
Problem 7. Data Encryption Standard
DES has expansion permutations and permuted choices (PCs).
We would normally lose info with permuted choices, which
are used twice in each DES cycle.
[1pt] a) Where and how are PCs used?
Ans: PCs are used once in selecting 48 bits of the 56-bit key to
use for a particular cycle. Although the PC is the same for
each cycle, the key itself is permuted each cycle (each half
is rotated left logically one or two bits on each cycle) so
the resultant 48-bit word uses different bits in different
places each cycle.
The other place PCs are used is in the S-boxes, where the
48-bit expanded right half of the (partially encrypted data)
is selected down to 32 bits (after combining it with the
48-bit cycle key). This is not so much a PC as a 32-bit
encoding of a 48-bit quantity that has in it some redundancy.
(That is, there is not really a mapping of some of the input
bits to the output bits with some inputs dropped, but all of
the input bits help select the output bits....)
[2pt] b) Show that information is not lost when PCs are used in DES.
Ans: The PC applied to the key to get the cycle key does not affect
the data directly - only key info is lost, but that is OK as
the receiver already has the whole 56-bit key.
In the S-boxes, recall that the 48-bit intermediate result is
taken as 8 6-bit blocks, each of which produces a 4-bit code
out of the S-box, to provide a 32-bit result. Where did these
6-bit blocks come from? They are the result of XORing the
48-bit cycle key (no info loss there) with the result of the
expansion permutation applied to the 32-bit right half of data.
This EP has a critical property - it takes the 32-bit input as
8 4-bit blocks, each of which is expanded to a 6-bit block by
taking the "nearest" bit on the end of the two adjacent blocks
(including "wrap-around" so block 7 is adjacent to block 0) -
the two end bits are redundant. In the S-boxes, the two end
bits (after XORing with the cycle key) are then used to select
the row, while the 4 center bits select the column. In essence,
the two redundant bits select a mono-alphabetic substitution,
while the 4 center bits are the symbol being encoded in the
4-bit output of the S-box. Thus no info is lost.
[2pt] c) Relate DES to Shannon's observations about product ciphers.
Be specific in showing how DES satisfies the desired properties.
Ans: Product ciphers are the result of concatenating a substitution
cipher with a transposition cipher. This can result in a much
stronger cipher than either cipher taken alone, or the result
of concatenating two ciphers of the same type.
DES alternates transposition with substitution in each cycle,
along with the XOR with the cycle key. If we simplified DES to
use 32-bit cycle keys, then we would have an XOR with the cycle
key, then a substitution (only one, not one of 4), followed by
a transposition (the P-box). DES complicates this slightly with
the EP/PC/S-Box approach which uses 48-bit intermediate results,
but the basic scheme of each cycle is a product cipher.

 we have
we have  (h) =
(N-1 ·
[(6-1.833)2 + (4-1.833)2 +
2 · (3-1.833)2 +
2 · (2-1.833)2
(h) =
(N-1 ·
[(6-1.833)2 + (4-1.833)2 +
2 · (3-1.833)2 +
2 · (2-1.833)2  = 1.34 .
= 1.34 . 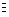 0 mod m,
where m denotes the keyword length.
0 mod m,
where m denotes the keyword length.