Refresher of Security Taxonomy
A list of basic terminologies frequently used with security & privacy related discussions/articles/research papers
-
Principal : A legitimate actor of any system.
-
Credential(s) : An artifact(s) to provide identity.
-
Authentication : The process through which an identity is associated with some principal.
-
Authorization : A set of rights/permissions which a principal possesses.
-
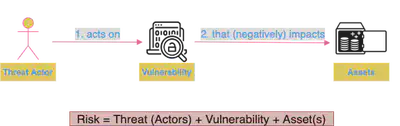
Threat : A specific means by which an attacker can put a system at risk.
-
Threat model : A collection of threats that is deemed important for a particular environment. It can also be thought as a collection of attacker(s) abilities.
-
Vulnerability : A systematic artifact that exposes the user, data, or system to a threat. Vulnerabilities are also known as attack vectors which an adversary (bad guy(s)) use to compromise a system. Common sources of vulnerability could be bad software/hardware design, bad policy/configuration, system misuse etc.
-
Attack : An occurrence where a vulnerability is exploited by an adversary. When an attack is successful, we call it as a compromise.
-
Risk = Threat (Actors) + Vulnerability + Asset(s)
-
Trust : An expectation from a principal to act in an anticipated manner.
-
Trust model : An explicit assessment of the trust embodied in a system.
-
Security model : A combination of a trust and threat models that address the set of perceived risks along with security requirements.
-
Confidentiality vs Privacy: Privacy applies to the person while confidentiality applies to the data (more here).