
Figure HW-2.1a. DES configuration for Problem 3.1, where
 denotes the initial permutation.
denotes the initial permutation. Note that in Step 3 (Decryption), f is applied to L, but not to R.
In this homework, we cover some important properties of the DES transformation. All problems are taken from the textbook (Stinson).
Answer: Since Li = Ri-1 and Ri = Li-1 XOR f(ki,Ri-1), and for decryption we know Li, Ri, and ki, we can compute
Ri-1 = Li
Li-1 = Ri XOR
f(ki,Ri-1) =
Ri XOR
f(ki,Li) .

Figure HW-2.1a. DES configuration for Problem 3.1, where
 denotes the initial permutation.
denotes the initial permutation.
Note that in Step 3 (Decryption), f is applied to L, but not to R.

Figure HW-2.1b. Details of DES configuration for Problem 3.1: (a)
role of initial permutation, and (b) two-stage computation.
Note: In b), if L and R are reversed
after
 , then they remain reversed through
all 16 stages.
, then they remain reversed through
all 16 stages.
 -1(R16,L16).
In the final stage of decryption, these partitions are again reversed.
-1(R16,L16).
In the final stage of decryption, these partitions are again reversed.
Problem 3.2. Let DES(a,k) represent the encryption of
plaintext a with key k using the DES cryptosystem. Suppose
c = DES(a,k) and
cc = DES(a',k'),
where (') denotes bitwise complement. Prove that
cc = c' (i.e., if we complement the
plaintext and the key, then the ciphertext is also complemented). Note
that this can be proved using only the "high-level" description of DES --
the actual structure of S-boxes and other system components are irrelevant.
Answer: The permutations, expansion permutation (EP), selection permutation or permuted choice (PC), key rotations and key selection permutation all behave the same regardless of their input, since DES is closed under complement. Thus, a bit complemented in the input will be complemented in the output, at the position assigned to that bit. This is not true of the S-box computation.
Letting a {0,1}X
and denoting the unitary vector on X as 1 = (1,1,...,1),
note that the complement of a is given by
a
{0,1}X
and denoting the unitary vector on X as 1 = (1,1,...,1),
note that the complement of a is given by
a' = 1 XOR a. Letting
b {0,1}X, we have
{0,1}X, we have
a' XOR b' =
1 XOR a XOR
1 XOR b =
a XOR b ,
a' XOR b =
1 XOR a XOR b =
(a XOR b)' .
' and
R0'. Since Li = Ri-1,
we will obtain Li' after each stage with
Ri-1' as input. If we let A = Ri,
B = EP(A), C = B XOR ki, D = S(C)
where S denotes an S-box, and E = PC(D), then if Ac =
A' and Bc =
B' (i.e., the EP or expansion
permutation preserves complement), then
Cc =
B' XOR ki' =
B XOR ki = C.
' and
Ec = E'). Due to the fact that, after the
i-th stage, the output's right partition
Ri = Ec
XOR Li-1' =
E XOR Li-1' =
Ri' ,
', R16') will result
in the DES output being the complement of the ciphertext.

Figure HW-2.2a. Dataflow and complement relationships for DES
using complemented keys and ciphertext. Note that the output of the XOR
operation (denoted by C/C) is not complemented.

Figure HW-2.2b. Single DES stage that illustrates the method
by which complement relationships in Figure HW-2.2a are obtained.
', then EP(A')
= EP'(A). Therefore, bits are merely shuffled and
copied, regardless of their value. ', since C =
B XOR J and
' =
B XOR 1 ' =
J XOR 1 '
XOR E = 1 XOR Li-1
XOR E, which implies that '.
Problem 3.3. One way to strengthen DES is by double encryption: Given two keys k1 and k2, and a binary input vector a, define c = ek1(ek2(a)), which is merely the product of DES with itself. If it happened that the encryption function ek2 was the same as the decryption function dk1, then k1 and k2 are said to be dual keys. (This is very undesirable for double encryption, since the resulting ciphertext is identical to the plaintext). A key is self-dual if it is its own dual key. (Do (a) and (d) only.)
Note: Dual keys (denoted by k and k~),
are those keys for which the key schedule of k~ is
the reverse key schedule of k.
3.3a. Prove that if C0 is all zeroes or all ones and D0 is all zeroes or all ones, then k is self-dual.
Answer: If the key is all zeroes or all ones, then all intermediate keys are the same, and the key is self-dual.
3.3d. Prove that the following pairs of keys (given in hexadecimal notation) are dual:
E001E001F101F101 01E001E001F101F1
FE1FFE1FFE0EFE0E 1FFE1FFE0EFE0EFE
E01FF01FFF10FF10 1FE01FE00EF10EF1
Answer: Simply confirm that the key schedule
of k is the reverse of k~.
Problem 3.5. Suppose a sequence of plaintext blocks is encrypted using DES, producing a corresponding sequence of ciphertext blocks. Let one ciphertext block be transmitted incorrectly (i.e., some ones are inadvertently changed to zeroes and vice versa). Show that the number of plaintext blocks that will be decrypted incorrectly is equal to one if ECB or OFB modes were used for encryption; and equal to two if CBC or CFB modes were used.
Answer: In ECB and OFB modes, the only input to a ciphertext block is the plaintext block corresponding to it (and the keys for DES, the initial vector, etc.) Thus, only one ciphertext block will be affected by a plaintext block, and vice versa.
In CFB and CBC, chaining is used, so multiple blocks will be affected.
Referring to the following figure, if (in CBC mode) a ciphertext block
ci' 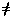 yi, then the corresponding intermediate key
xi
yi, then the corresponding intermediate key
xi' will be incorrect (assuming that the preceding
stage ci-1 was correct). Since
xi+1' = yi' XOR
dk(yi+1)
' will be incorrect. Since xi+2
only depends on yi+1 and yi+2, the intermediate key
xi+2 will be correct.

Figure HW-2.5. DES CBC encryption mode.
L0' = 0020000816 R0' = 0000040016
L1' = 0000040016 R1' = 0000000016
L2' = 0000000016 R2' = 0000040016
L3' = 0000040016 R3' = 0020000816
Answer: Following through the computations as given in the book, we have that
L0' = 2000000016 R0' = 0000000016
L1' = 0000000016 R1' = 2000000016
with p1 = 1. Answer part (b) only.Answer: Following through the computations as given in the book, we have that
This concludes the assignment for Homework #2, Fall 1996. If you have a question,please feel free to ask the instructors via E-mail or in class.