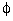 ,
,
 or
angular frequency
or
angular frequency
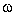 =
2
=
2
 ,
,
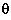 , and
, and
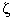 .
.
We begin our discussion of quantum cryptography (QC) by reviewing several topics pertinent to quantum mechanics. In Section 4.2.2, we discuss the mechanism and principles of secure key transmission based on quantum mechanics. Section 4.2.3 contains a brief discussion of issues involved in secure optical encoding based on concepts derived from QC theory.
"Quantum transmissions [one or more streams of particles upon which information is encoded] ... can be suppressed or altered but cannot in principle be monitored without disturbance."
What does this mean?
Note that the uncertainty principle holds only at quantum scales (i.e., in layman's terms, smaller than an atomic diameter). Additionally, as a result of much misinterpretation and deceptive (sci-fi) literature, there currently exists a class of pseudoscientists who gull people into believing that they can apply the uncertainty principle (and concepts that vaguely resemble early notions of wave functions) to various macroscopic phenomena. For example, various "New Age" groups consider themselves able to "direct waves" (whatever that means) using crystals, plastic pyramids, and suchlike. That drivel should not be confused with quantum physics, and bears no relationship whatever to this discussion.
Quantum cryptography has the following features (in theory):
The foregoing approaches are infeasible in quantum cryptography, because:
We next discuss physical and theoretical bases for encoding information in quantum cryptosystems.
Definition. In modelling photonic (i.e., lightwave) propagation, it is useful to recall the five primary properties of an electromagnetic wave, which are:
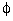 ,
,
 or
angular frequency
or
angular frequency
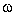 =
2
=
2
 ,
,
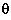 , and
, and
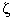 .
.
Assumption. In practice, we generally assume that a QC light source is coherent, since lasers are typically employed as light sources in fiber optical communication applications. Hoever, when we later discuss the phenomenon of modal dispersion in optical fibers, we shall see that coherence can be disrupted by simple physical phenomena.
Definition. For purposes of simplicity, we can express lightwave intensity as
I = Io · sin(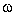 t +
t +
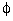 ) ,
) ,
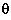 understood.
understood. Observation. Polarization can be linear or circular. Light is linearly polarized in one of two orthogonal directions - horizontal or vertical. Similarly, circular polarization can have two directions - left- or right-circular. We can visualize the effects of linear polarization by modelling light in terms of a vertical electric field (E-field) axis and horizontal magnetic field (B-field) axis, as shown in Figure 4.2.1.

Figure 4.2.1. Light propagation modelled as vertical (horizontal)
electric (magnetic) field components. The linear polarizer with axis vertical
passes only the vertical oscillations (bold wavy line).
Definition. The symbol h denotes the quantity
h/2 , where h denotes
Planck's constant. Niels Bohr first introduced this concept in his theory
of the hydrogen atom.
, where h denotes
Planck's constant. Niels Bohr first introduced this concept in his theory
of the hydrogen atom.
Observation. The angular momentum of an alectron due to its spin ps is assigned the value
ps = s · h ,
where s has value 1/2, which typifies particles called fermions (e.g., electrons, protons, and neutrons). These are also called spin-1/2 particles.Observation. A distinguishing feature of spin-1/2 particles is the conformance of their energy distribution to Fermi-Dirac statistics. Particles whose spin is an integral multiple of h or zero are called bosons (e.g., alpha particle of spin zero and deuteron of spin one). The energy distribution of bosons is described by Bose-Einstein statistics.
Remark. Given the quantum number s, the magnitude of the electron's spin angular momentum is computed as
h(s(s+1))1/2 = h · s1/2/2 .
Definition. A QC encoding basis is a two-valued parameter that characterizes some measurable property of a physical entity.Example. Vertical or horizontal polarization of light waves (and, hence, of their dual particle or photon representation) is a QC encoding basis. Phase angles separated by 180o are also QC encoding bases.
Definition. Conjugate encoding bases are two QC encoding bases such that, when a basis is measured for a given particle that does not carry information in the context of that particle, both possible outcomes of the measurement have probability 1/2.
Example. When phase angles are used as encoding bases, the conjugate bases can be separated by 90 degrees. For example (0,180) degrees and (90,270) degrees.
We next consider four instances of quantum cryptosystems, and discuss such systems in terms of two unifying models.
From the preceding list, it is easily seen that quantum cryptosystems can be partitioned into EPR and non-EPR classes. The following table and algorithm (from Reference [2]) helps clarify basic procedure.
%%%TABLE GOES HERE%%%where Steps 1-10 refer to:
Observation. If we have two polarization bases (e.g., vertical/horizontal linear and left/right-hand circular polarization), then if an adversary tries to measure the v/h basis, the information encoded on the l/r polarization basis is destroyed. By measuring in the wrong basis, the adversary obtains no information, since the bits of interest are destroyed due to alteration of the respective photons' physical properties by interaction of the observer and the photons.
Remark. If an adversary guesses the basis wrong, then retransmission of the intercepted particle (assuming this is possible) yields one or more bit errors (assuming error detection codes or related capabilities at the receiver). Thus, an error can be detected at the receiver, which could imply eavesdropping, but could also result from other effects, such as physical damage to the transmission channel.
Current approaches to QC include frequency-division long-distance interferometry (FDLDI), which has the following features:
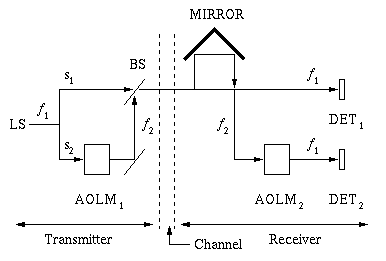
Figure 4.2.2. Schematic diagram of optical quantum
encoder/decoder for secure key transmission, where LS = Light Source,
AOLM = Acousto-Optic Light Modulator, DET = Detector, and BS =
Beam Splitter. Here, f2 > f1 has
been reported in the literature.
 , k
, k
 Z. MZ also coerces
s2 to have phase
k
Z. MZ also coerces
s2 to have phase
k , so there is destructive
(constructive) interference at DET1 or DET2
(DET2 or DET1). The AOLM2
downshifts s2 to frequency f1.
, so there is destructive
(constructive) interference at DET1 or DET2
(DET2 or DET1). The AOLM2
downshifts s2 to frequency f1. If you an adversary (Oscar) listens to the channel and guesses the encoding basis correctly, Oscar obtains one bit of information. This also holds for the receiver. If the basis is guessed incorrectly, the bit value is irretrievably lost. Thus, if Oscar measures the intercepted photons incorrectly, they are irretrievably lost and yield a completely random output due to the conjugate encoding bases. This is the only reason that eavesdropping can fail in QC systems.
4.2.3.1.1. Modal dispersion in fiber optic cables results from internal reflection of light carried inside the cable. This effect causes an optical path inside a cable of length L to be of physical length greater than L. Figure 4.2.3 schematially illustrates the geometry and physical consequences of this effect.
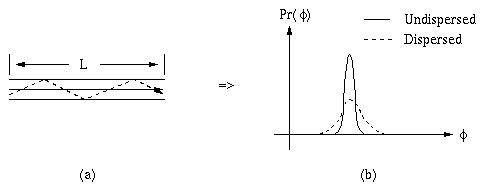
Figure 4.2.3. Schematic illustration of the effects of
modal dispersion in fiber optic cables: (a) ray propagation
geometry; and (b) broadening of the initial phase probability
distribution (solid line) associated with a photon having
nominal phase 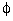 . The resultant
probability distribution is shown as symmetric, due to possible
reflection about the principal value range of
. The resultant
probability distribution is shown as symmetric, due to possible
reflection about the principal value range of
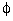 .
.
4.2.3.1.2. Errors due to eavesdropping can increase the measured error rate at the receiver due to (a) choice of the wrong basis by an adversary monitoring the channel, and (b) dispersion or attenuation introduced into a fiber-optic channel by physical intrusion into the optical fiber. Since small changes in the error rate may be hard to detect in practice (e.g., due to time-variant dispersion effects that result from fiber deformation, hydration, etc.), a given fiber channel must be well characterized prior to being used for QC purposes. This is a nontrival measurement, but is of great importance, since the communicating parties may subsequently have difficulty distinguishing normal channel errors from those introduced by an adversary.
A conservative perspective on the security of QC would assume that every error measured at the receiver is caused by an adversary. Based on the number of errors observed at the receiver, an upper bound can be derived for the amount of information that an adversary could observe. Given this upper bound, Slutsky and Fainman [-] propose to employ privacy amplification, an information-theoretic technique, to maximize the amount of received information.
For example, suppose Alice transmits 1000 bits to Bob and Oscar knows 110 bits of a given transmission. Privacy amplification allows one to manipulate the remaining 890 bits (via the use of checksums, etc.) to render such bits secure.
4.2.3.1.3. Detection of individual photons has traditionally been implemented with photomultiplier tubes (PMTs). Unfortunately, fiber-optical communication employs light whose wavelength is primarily in the red and infrared (IR), where the detection efficiency and sensitivity of PMTs is low. Hence, avalanche photodiodes will probably be employed in the near future, due to their enhanced quantum efficiency in the IR.
4.2.3.1.4. Throughput of a typical QC system generally depends upon
Observation. A typical avalanche photodiode currently exhibits a bandwidth that is constrained by a 50ns cycle time. This implies a maximum raw throughput of 20MHz.
Example. If the channel bit error rate (BER) is 5 percent and channel loss over the propagation path is 10db, then the current throughput expectation is approximately 104 to 105 bits per second.
4.2.3.1.5. Choice of basis may be performed by the transmitter, in a random fashion. Additionally, the receiver may choose randomly from two conjugate bases. In such cases, half the bits are lost due to basis mismatch at the receiver. In order to properly decode bits at the end of the transmission, communicating parties transmit a list of bases used in the transmission.
Recall that an adversary cannot measure the transmitted photons without inducing erroneous bits at the receiver. Thus, a posteriori exchange of bases does not compromise security since:
[1] Ekert, A.K. "Quantum cryptography based on Bell's theorem", Physics Review Letters 67(6):661-663 (1991).
[2] Bennett, C.H. "Quantum cryptography based on Bell's theorem", Physics Review Letters 67(6):661-663 (1991).
[3] Cagnac, B. Modern Atomic Physics: Quantum Theory and its Applications, translated by J.S. Deech, New York: Wiley (1975).
[4] Levich, V.G. Theoretical Physics: An Advanced Text, translated by S. Subotic, Amsterdam: North-Holland (1971).
Click here for Giles Brassard's extensive bibliography of quantum cryptography. (More information to follow.)
Brassard is an imaginative scientist, and has contributed to early work in Quantum Teleportation at IBM.
You may also want to check on IBM's Quantum Communication and Computation Web page, which has several links to other sites.
This concludes our overview of quantum cryptosystems.